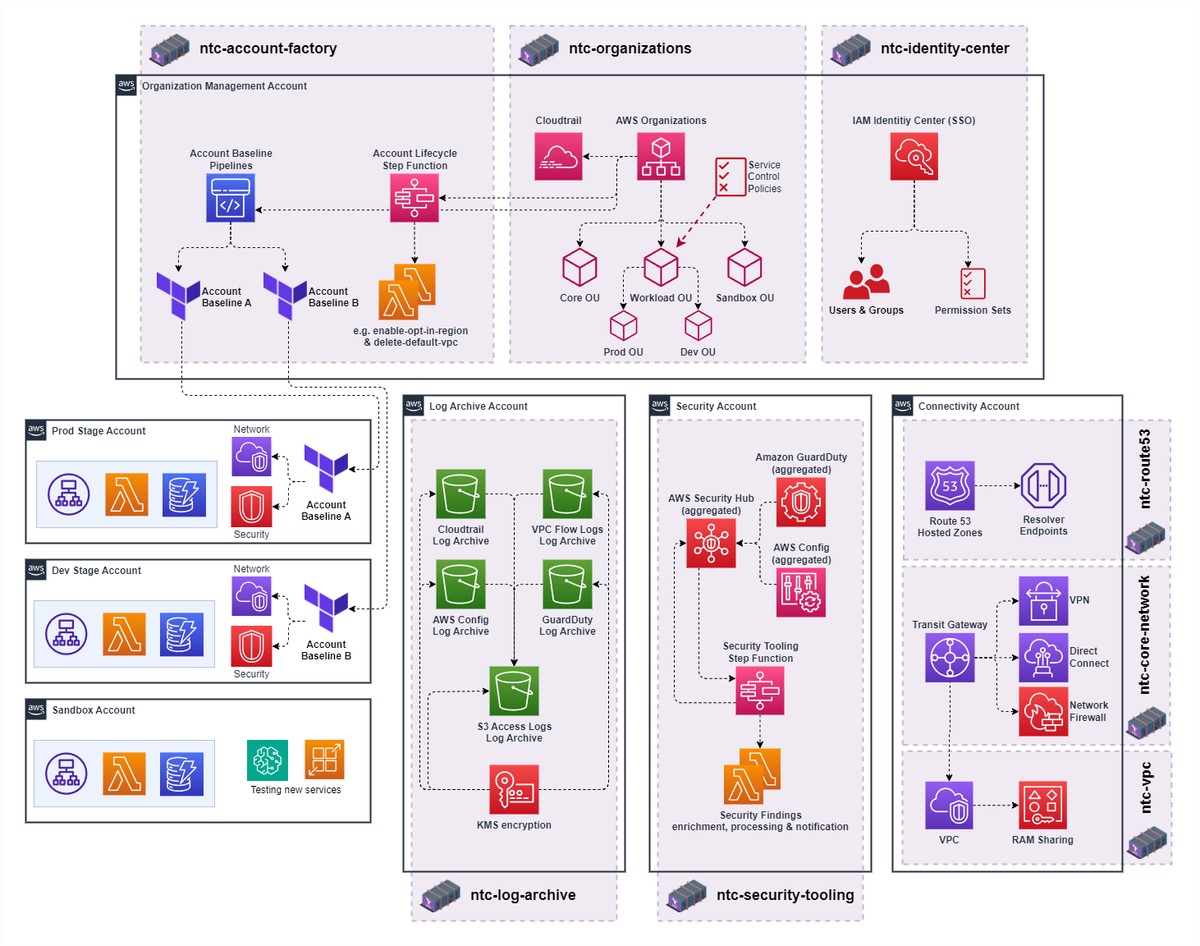
Nuvibit Terraform Collection (NTC)
NTC is a revolutionary AWS Landing Zone & Foundation solution based entirely on Infrastructure as Code with Terraform. NTC is specifically designed to deploy and manage an enterprise-ready, compliant and scalable AWS environment. Our flexible, declarative, and modular approach offers many unique benefits to a platform engineering team and drastically reduces implementation time and effort.
Revolutionize your AWS infrastructure with streamlined management, accelerated deployment, and GitOps best practices.