RWE is a leading global energy company known for the production and distribution of both conventional and renewable energy. Operating in several regions, RWE has a strong presence in Europe, North America, and Asia. The company manages a complex AWS multi-account configuration, involving around 200 AWS accounts spread across four AWS regions and utilized by diverse development teams. RWE places great emphasis on digital security and integrates various AWS services, such as AWS Config, AWS Security Hub, and Amazon GuardDuty. Every week, their Security Operations Center (SOC) receives nearly 1 billion AWS CloudTrail events that feed into their SIEM system.
The SOC team faces the challenge of efficiently prioritizing and processing a large number of security findings across numerous AWS accounts. Many of these findings relate to accepted risks, which adds complexity and time to the task. To address this issue, RWE aims to categorize AWS accounts based on their security levels, such as production, non-production, and departmental accounts. They also intend to enrich the security findings with essential information, like the individual responsible or the security status of the source account. Automation is another key focus for RWE. They plan to roll out new rules to subsets of accounts, define automated actions, and apply specific event filters. Furthermore, RWE places a high value on ensuring that all configurations are auditable and revision-proof to meet their company-specific compliance requirements.
RWE decided to introduce our serverless solution SEMPER in their AWS Organization.
Through GitOps, the customer can specify security policies (Documentation on SEMPER Policies) that automatically manage the lifecycle of their AWS Security Findings.
SEMPER operates entirely within the customer’s environment.
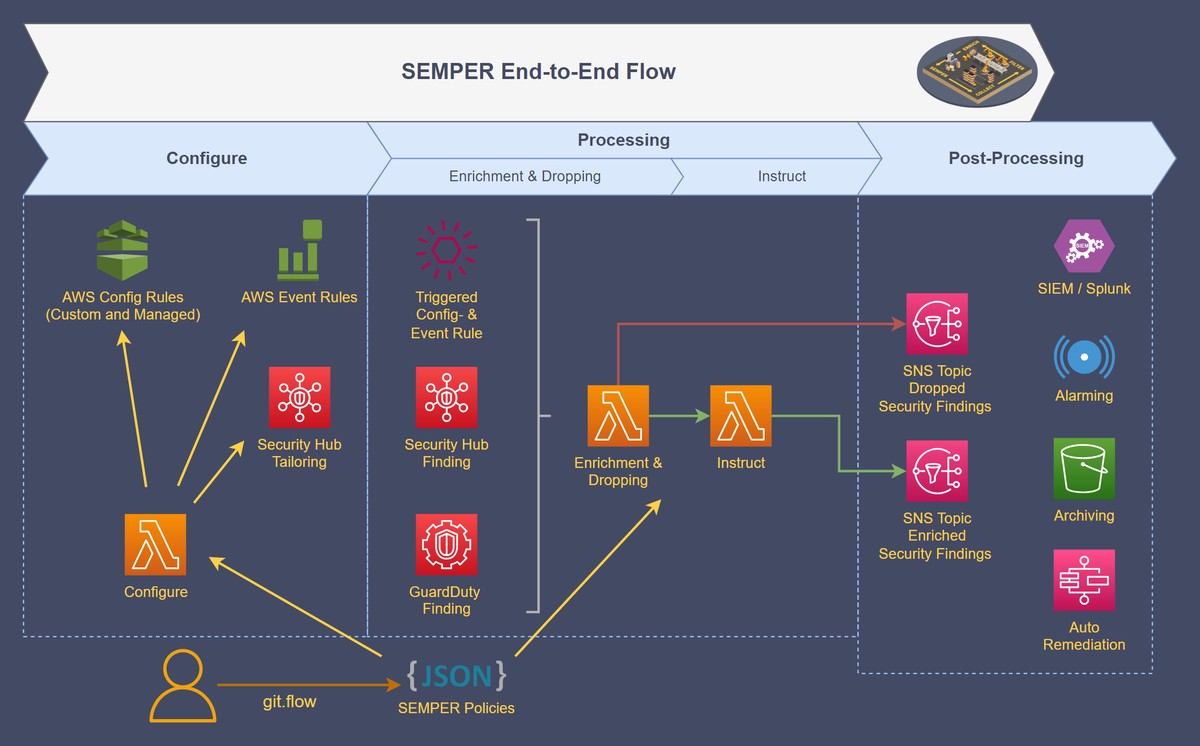
- Configure: Targeted deployment of AWS Config, AWS EventBridge rules, and AWS Security Hub controls.
- Processing: Enriching and filtering of AWS Security Findings.
- Post-Processing: Archiving and additional workflow automation, such as alarming and auto-remediation.
- Swift Policy Implementation: New rules or modifications can be integrated seamlessly into the entire landscape within minutes.
- Advanced Automation: The entire findings lifecycle benefits from automated policies, streamlining detection, analysis, and response processes.
- Enhanced Traceability: Policies describe accepted risks and exceptions. This ensures traceability and easy access to historical data.
- Richer Context: Additional contextual data related to security findings supports automated and manual triage processes, resulting in faster and more informed decisions.
- Relevant Focus: By filtering unimportant events, the SOC team can now focus exclusively on relevant Security Findings, streamlining their workflows and ensuring timely response.
- Facilitated Auto-Remediation: Wherever appropriate, issues can now be remediated automatically, minimizing manual effort and improving response times.
- Increased efficiency in processing security findings: Customer can focus on the 0.1% security findings that are truly relevant (compared to the number of AWS CloudTrail events).
- Staff Productivity: Significant time savings for SOC staff.
- Automated Interventions: Thousands of auto-remediations triggered per week.
- Reduced Engineering Efforts: Remarkable reduction in workload.
- ROI: Significant return on investment.
